AI Security Practices
At BlendVision, we prioritize transparency about our AI products with our customers. Here’s an outline of our functionality, data protection, and privacy practices.
How Does Our AI Work?
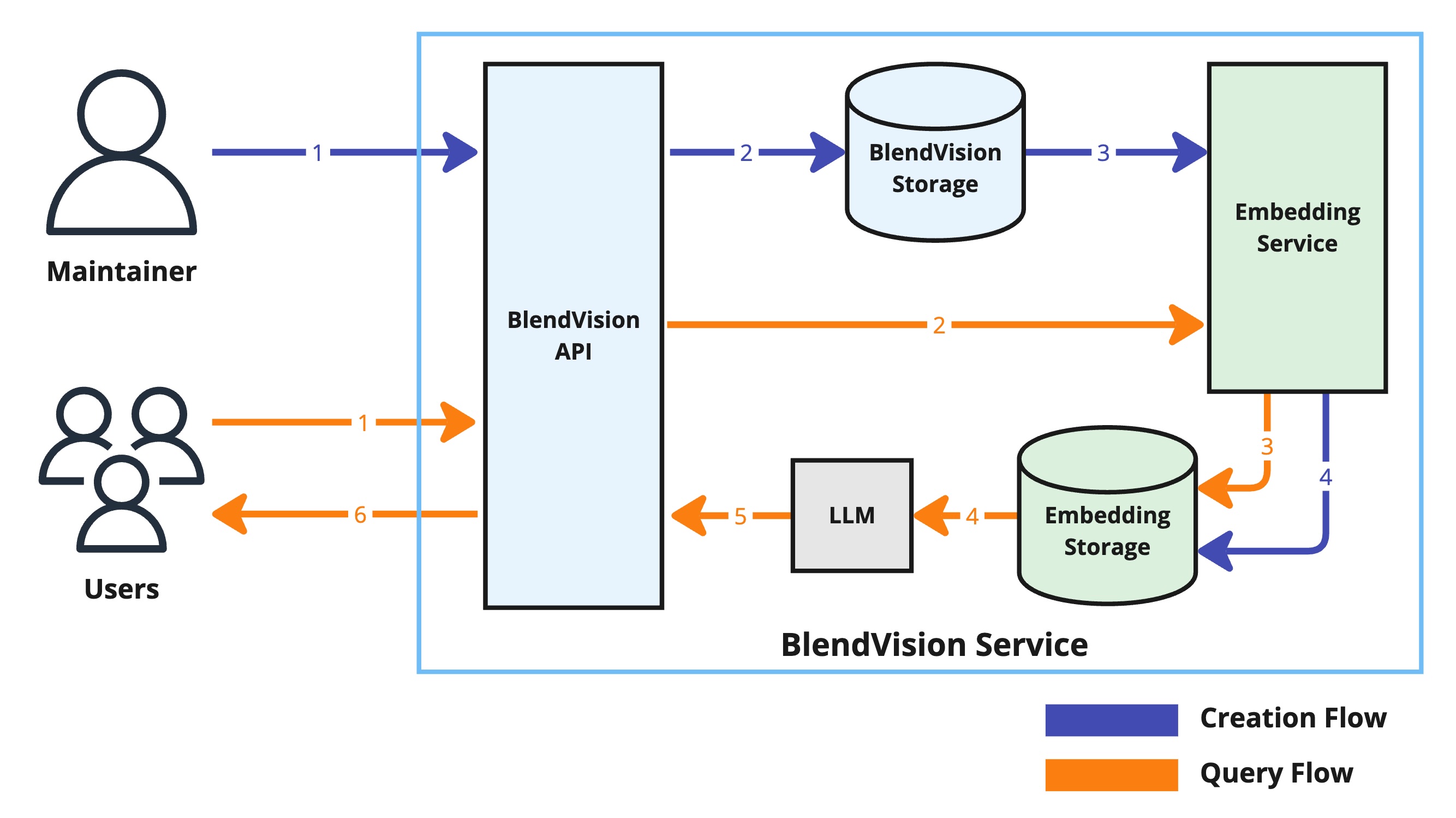
Source Data Creation Flow (Blue Lines)
- Upload: Maintainers upload the source data to BlendVision Service. This is the first step in processing and embedding data.
- Storage: Once uploaded, the data is forwarded and securely stored in BlendVision Storage. This ensures the data is safe and ready for further processing.
- Embedding: The Embedding Service processes the stored data to generate embeddings. Embeddings are numerical representations of the data that our AI can understand and use.
- Embedding Storage: These embeddings are then stored for future use, particularly for quickly retrieving relevant information when a user makes a query.
Security Measures:
- Identity Verification: To protect data, we ensure that only authorized users with verified identities can access it.
- Access Control List (ACL): ACLs help manage who can access specific digital environments. Through content permission management, BlendVision can control access to individual pieces of content, managing permissions for users and groups using our interface. Permissions can be customized, allowing isolation of organizations or enabling cross-team access.
- Encryption: All data transmission is encrypted using SSL/TLS protocols, ensuring secure communication over the internet. Data within our databases is also protected with access controls and audit logs.
- Data Usage: We protect data from unauthorized use. Data will be deleted upon organization deactivation, with a 1-month buffering period to ensure retention for necessary purposes. Event logs are maintained for auditing and ensuring data traceability and proper usage.
User Query Flow (Orange Lines)
- User Query: Users interact with our Chatbot by sending queries.
- Embedding Processing: The Embedding Service processes these queries to find the most relevant embeddings that match the user's request.
- Embedding Retrieval: The system retrieves these relevant embeddings from storage.
- Large Language Model (LLM) Processing: The LLM processes these embeddings to generate meaningful responses or answers.
- Result Preparation: The results are prepared for delivery to the user.
- Response Delivery: Users receive the information or answers they requested, completing the query process.
What Does BlendVision’s Large Language Model (LLM) Provide?
BlendVision leverages advanced Large Language Models (LLMs) to deliver high-quality responses and insights. We continuously evaluate various LLMs to ensure the best experience for our users. When users send a query via Chatbot, it is processed by the Embedding Service to search within the embedding storage. Citations and responses are generated by the LLM processor and provided back to the users, ensuring they receive accurate and relevant information without compromising data security.
Key Features of Our LLM
- High-Quality Responses: Our LLM is designed to provide accurate, relevant, and meaningful answers to user queries.
- Customer Data Confidentiality: We ensure that customer confidential data is not stored outside of BlendVision’s service. This means that data processed by our LLM remains within our secure infrastructure, maintaining strict data privacy standards.
- Data Privacy: We ensure that customer data is handled securely and in compliance with privacy regulations.
- Continuous Improvement: We regularly update and improve our LLM to maintain the highest standards of performance and reliability.
With our LLM, users can trust that they are receiving reliable information while their data remains protected.
Data Protection and Privacy Practices
Our comprehensive data protection and privacy practices are designed to safeguard your information at every stage, from collection to deletion. We adhere to stringent standards to ensure that your data is used appropriately and remains secure. Below, we outline the key components of our data protection strategy.
Data Protection:
- Purpose Limitation: We strictly use data for providing and improving our services. BlendVision does not use user data for AI training or any other purposes outside of the agreed service scope.
- Traceability and Auditing: Detailed event logs are maintained for auditing purposes, ensuring data traceability and confirming proper data usage.
- Data Retention: Data will be deleted once the organization is deactivated, with a 1-month buffering period for retention to handle any final requirements or recovery needs.
Confidential Data Protection:
- Encryption: All data is encrypted during transmission (via SSL/TLS) and at rest (with industry-standard protocols), ensuring data security both in transit and storage.
- Access Control: We implement strict access controls, including ACLs and identity verification, ensuring only authorized users can access data.
- Tenant Isolation: Data is isolated per tenant, preventing cross-access between different organizations using our services and maintaining data integrity.
- Regular Security Audits: We regularly conduct security audits to ensure the confidentiality and integrity of your data, identifying and mitigating potential risks.
Data Audits:
- Vulnerability Assessments: Regular vulnerability assessments (SAST) are performed to identify and address potential security risks, maintaining data integrity.
- Regular Backups: We leverage the backup mechanisms provided by our cloud solutions, ensuring data recovery capability in case of disasters or unforeseen events.
Data Location:
- Our data is stored in cloud providers' facilities located in various countries. These locations are chosen for optimal performance and compliance with regional data protection regulations.
Source Data Management
At BlendVision, we have implemented robust source data management practices to ensure the integrity, security, and proper usage of data sources in our query processes.
- Enhanced Access Control: Our practices allow for more granular control mechanisms, ensuring that only authorized data sources are used.
- Improved Security: By managing source data effectively, we enhance the overall security and integrity of our AI systems, safeguarding them against unauthorized access and data breaches.
- Auditability: Our source data management provides robust audit logs, making it easier to track and review data access and usage.
- Scalability: These practices support scalable data management, allowing BlendVision to accommodate growth without compromising on data security and integrity.
For further details regarding our security policies and privacy practices, please refer to the Security Policy section on our website.