BlendVision Technical Infrastructure and Security
Architecture
Hardware and Software
BlendVision’s cloud service enables customers to utilize BlendVision software hosted on dedicated servers through Amazon Web Services (AWS). This setup provides extensive server options across North America, Europe, and Asia-Pacific, ensuring global accessibility. The BlendVision platform is designed to be secure, scalable, and highly available, providing redundancy to ensure consistent uptime and reliability. It leverages Amazon EC2 instances and Amazon Elastic Kubernetes Service (EKS) for container orchestration, Amazon S3 for content storage, and Amazon CloudFront as its content delivery network to optimize performance and delivery speed.
Amazon Content Backup and Disaster Recovery
BlendVision utilizes Amazon S3 for content backup and disaster recovery, ensuring 99.999999999% durability of objects annually. Data is redundantly stored across multiple Availability Zones, each with its own distinct and independent infrastructure. This setup enhances reliability by avoiding shared points of failure such as generators and cooling equipment. The physical separation of Availability Zones ensures that even rare disasters like fires, tornadoes, or flooding would only impact a single zone.
BlendVision Server Redundancy
BlendVision's cloud solution ensures redundancy across multiple Amazon Availability Zones, eliminating single points of failure and enhancing reliability. This architecture provides redundancy for all server types, including front-end, back-end, and database servers. BlendVision's relational database is mirrored across multiple Availability Zones within each region. If a single server goes offline, others remain operational. Similarly, if an entire Availability Zone experiences an outage, the architecture ensures continued availability from other zones, maintaining uninterrupted service for customers.
Business Continuity
BlendVision maintains a comprehensive response plan for security and business continuity incidents. This plan encompasses all stages of incident response, including preparation, identification, containment, eradication, recovery, and root cause analysis. To ensure effectiveness, the plan is tested annually, equipping a trained team to respond swiftly and minimize the impact of incidents, facilitating a rapid return to normal operations.
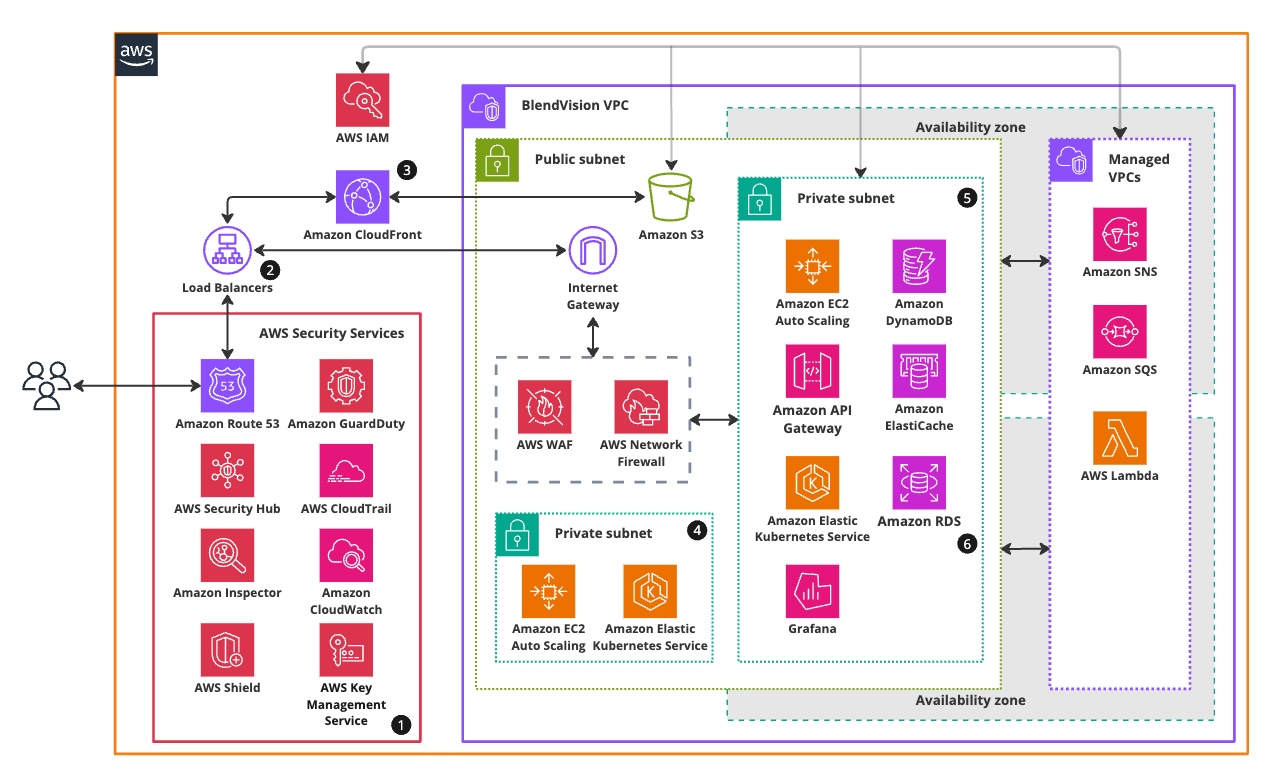
Architecture Overview
1. Comprehensive Security Suite
BlendVision employs a robust set of security services to protect its cloud infrastructure and data. This includes Amazon Route 53 for reliable DNS and traffic management, AWS Security Hub as a centralized security dashboard, GuardDuty for threat detection and alerts, and AWS Inspector for automated security assessments and vulnerability identification.
2. Efficient Traffic Management
HTTPS requests are managed by Application Load Balancers, distributing traffic across multiple BlendVision servers in various Availability Zones. This setup ensures fault tolerance and seamless load balancing to efficiently handle incoming user traffic.
3. Global Content Delivery
Amazon CloudFront CDN utilizes a global network of edge locations and regional caches to store content closer to viewers, ensuring faster performance. BlendVision stores resources and static content in Amazon S3, providing a highly durable storage infrastructure available across all Availability Zones.
4. Internal Infrastructure for Enhanced Services
BlendVision leverages Amazon EC2 instances and Amazon EKS (Elastic Kubernetes Service) within private subnets to support key functions such as encoding, live streaming, and AI processing. EC2 provides scalable computing capacity, enabling efficient handling of dynamic workloads. EKS manages containerized applications, ensuring seamless orchestration and deployment of microservices, which enhances the platform's scalability and operational efficiency.
5. Scalable and Reliable Server Management
BlendVision deploys multiple autoscaling front-end and back-end server types across multiple Availability Zones, ensuring reliability and redundancy. This setup allows for on-demand scaling to accommodate increased traffic and processing needs efficiently.
6. Robust Database Management
BlendVision's SQL databases are located in multiple Availability Zones, featuring synchronous high-safety database mirroring with automatic failover. This configuration ensures reliability and fault tolerance.
Security
Amazon EC2 Security
Amazon EC2 provides compute capacity with security features such as security groups and IAM roles. Security groups act as virtual firewalls, and IAM roles manage secure access to AWS resources. BlendVision utilizes Amazon EC2’s security groups to enforce strict access controls by allowing traffic only from trusted IP ranges and necessary ports, minimizing the attack surface. IAM roles are used to grant EC2 instances temporary, limited-time access to AWS resources, reducing credential exposure and enhancing security.
Network Security
- Distributed Denial of Service (DDoS) Attacks
To protect against DDoS attacks, BlendVision utilizes AWS Shield Advanced, which offers comprehensive protection for their applications. This service provides real-time visibility into threats and integrates with AWS WAF for additional layer 7 protection, ensuring that their services remain accessible and performant during large-scale attack attempts.
- Man In the Middle (MITM) Attacks
BlendVision mitigates the risk of MITM attacks by enforcing the use of secure communication protocols such as HTTPS and TLS across all data transmissions. This ensures that data exchanged between users and BlendVision's applications is encrypted and secure from interception. They also utilize AWS's VPN capabilities to establish secure, encrypted connections for data transfers between their on-premises systems and AWS infrastructure.
- IP Spoofing
AWS's network infrastructure inherently prevents IP spoofing by ensuring that instances can only send traffic from their assigned IP addresses. BlendVision adheres to these security measures by configuring their network settings and security groups to align with AWS best practices, thereby safeguarding against unauthorized IP address usage.
- Port Scanning
To defend against unauthorized port scanning, BlendVision employs a combination of AWS security groups and network ACLs. These are regularly audited and updated to restrict access to only necessary ports, effectively minimizing the risk of exposure to potential vulnerabilities and ensuring that their network remains secure from scanning attempts.
- Encryption
For data encryption, BlendVision utilizes AWS's robust encryption services to protect both data at rest and in transit. They implement server-side encryption for data stored in Amazon S3 and RDS, ensuring data confidentiality. Additionally, AWS Key Management Service (KMS) is used for secure key management, providing seamless integration with other AWS services to maintain data integrity and protect sensitive information.
- Network Isolation
BlendVision deploys their applications within Virtual Private Clouds (VPCs) to achieve network isolation. This setup allows them to define a custom network topology, including the configuration of subnets, route tables, and gateways, which enhances security by ensuring that their resources are only accessible within a controlled and isolated environment.
Cloud Application Security Assessment (CASA) Certification
BlendVision has successfully completed the Cloud Application Security Assessment (CASA) verification (Certification ID: 1a15fc0e). This certification is based on the OWASP Application Security Verification Standard (ASVS), which is an industry-recognized framework for enhancing application security:
- Comprehensive Vulnerability Assessment
Conducted thorough testing to identify and mitigate potential vulnerabilities across all applications.
- Strengthened Data Protection
Implemented robust encryption protocols and access controls to safeguard sensitive data against unauthorized access and breaches.
- Improved Application Integrity
Ensured the integrity of applications through regular code reviews and security audits, preventing tampering and ensuring reliable operation.
- Enhanced Authentication and Authorization
Upgraded authentication mechanisms to include multi-factor authentication, ensuring that only authorized users have access to critical systems.
- Increased Resilience Against Attacks
Developed and deployed security measures to defend against common attack vectors such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Compliance with Industry Standards
Achieved compliance with global security regulations and standards, providing assurance to customers and stakeholders about the security of BlendVision's services.